As mobile device management (MDM) evolves, so do the security features on mobile platforms like Apple iOS. One recent security enhancement from Apple starting with iOS 17.3 is called Stolen Device Protection (SDP). This feature adds an extra layer of security to protect iPhones and iPads from unauthorized access if they are lost or stolen. While this is great for device security, it has presented challenges for organizations using Microsoft Intune, especially for manual enrollment scenarios like Bring Your Own Device (BYOD).

Table of Contents
What Is Stolen Device Protection?
Stolen Device Protection requires additional verification such as Face ID and enforces a security delay if the device is away from trusted locations (e.g., home or work). When enabled, this protection causes a “security delay” that blocks installation of device management profiles for about one hour unless proper authentication is performed. This means when users manually enroll their iOS devices into Intune, the profile installation may fail or be delayed, causing a poor user experience. A screen shot of the delay message looks like this:
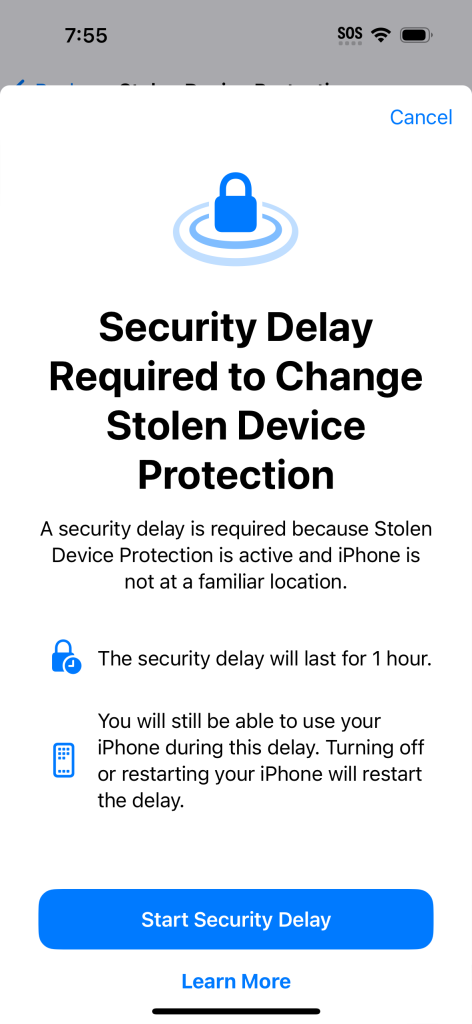
Why Is This a Problem for Intune Manual Enrollment?
Many organizations leverage Microsoft Intune to secure mobile devices and ensure compliance. However, for BYOD scenarios where users manually enroll their personal devices, the default Apple Stolen Device Protection can interrupt the enrollment process. Users trying to enroll their device remotely often face:
- An error or failed profile installation due to the security delay.
- The need to wait one hour after disabling SDP before enrollment can proceed.
- Confusion about why the enrollment is being blocked.
Currently, Stolen Device Protection cannot be bypassed or overridden automatically during manual enrollment. Unlike corporate-issued supervised devices managed through Apple’s Automated Device Enrollment (ADE), BYOD devices lack central control to manage or disable SDP remotely.
Current Workarounds
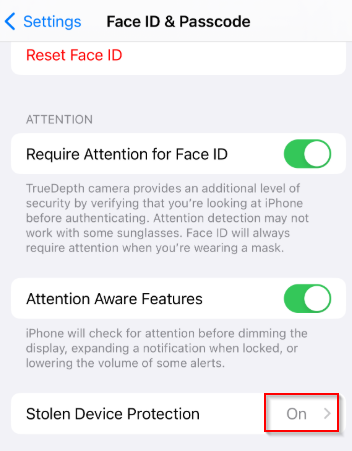
- Temporarily Disable Stolen Device Protection:
Users can manually turn off SDP on their iOS device under Settings > Face ID & Passcode > Stolen Device Protection, authenticate with Face ID or passcode, and then proceed with enrollment. However, disabling this security feature reduces device protection during the enrollment window and requires user cooperation.
- Wait Out the Security Delay:
After disabling SDP, there is a mandatory one-hour wait before the device accepts the management profile installation. Users must re-authenticate to finalize enrollment after this period. - Use Trusted Networks:
Some have observed that initiating enrollment from known trusted Wi-Fi locations (like the corporate network) can sometimes reduce enrollment delays or security prompts, though this is not a guaranteed solution. - Enroll Devices via Automated Device Enrollment (ADE):
The recommended method for corporate and managed devices is to use ADE through Apple Business Manager, which creates supervised devices that Intune can manage fully, including controlling Activation Lock and SDP features. This is not applicable in strict BYOD contexts. - Allow Limited Management Without Full Enrollment:
Organizations may allow app-level management such as App Protection Policies with only limited device control to avoid enrollment issues caused by SDP.
Why Is This Important?
The security benefits of Stolen Device Protection are significant in preventing theft-related data compromise. However, the friction it introduces in manual Intune enrollment creates operational headaches especially for BYOD policies. IT administrators and security teams must balance enforcing strong security with a smooth user experience during device onboarding.
Conclusion & Recommendations
- If possible, avoid manual BYOD enrollment for Apple devices with SDP enabled.
- Use Apple Automated Device Enrollment (ADE) for corporate devices whenever feasible.
- Educate users about SDP and enrollment delays to reduce confusion.
- Consider allowing app-level control such as App Protection Policies without full MDM enrollment where strict device control isn’t possible.
Microsoft and Apple will likely continue evolving these features, so staying informed on platform changes is key to maintaining robust yet user-friendly device management.
References
- Microsoft Docs on disabling Activation Lock and Intune enrollment: https://learn.microsoft.com/en-us/intune/intune-service/remote-actions/device-activation-lock-disable
- Community discussions about Stolen Device Protection and manual Intune enrollment challenges: https://discussions.apple.com/thread/255739233