Securing local admin passwords on macOS devices has long challenged IT teams especially in compliance-driven environments. With native support for LAPS (Local Administrator Password Solution) now available in Microsoft Intune, Mac management receives a substantial security upgrade.

Table of Contents
About LAPS
Securing local admin passwords on macOS devices has been a challenge for IT teams, especially in environments with strict compliance requirements. Now, with native support for LAPS (Local Administrator Password Solution) in Microsoft Intune, Mac management gets a serious security upgrade. Admins can automatically rotate unique, randomized passwords for local admin accounts across enrolled Macs, storing them securely in Microsoft Entra ID. This drastically reduces the risk of lateral movement during breaches and makes password auditing a breeze. It’s a simple but powerful way to enforce zero trust principles and protect sensitive endpoints without relying on custom shell scripts or third-party tools.
Pre-requisites
The following are requirements for the macOS LAPS Solution:
- macOS 12 and later
- Devices must be synced over to Intune from Apple Business/School Manager
- Enrollment via macOS ADE profile in Intune
Expected Behaviour
During my testing of the new tool, I observed that when Compliance and Device Restrictions policies are deployed with password requirements, users are prompted to change their password upon first login. I reported this to the Microsoft Intune Product team, and they confirmed that this behavior is expected regardless of whether the existing password is compliant. I will provide a more detailed explanation in my post.
Role-based access controls for macOS LAPS
To ensure the appropriate visibility and control, custom admin roles in Intune must include the following permissions, which are not part of the built-in roles.
Navigate to Enrollment Programs and set the following options to Yes.
- View macOS admin password
- Rotate macOS admin password

Configuration & Admin Experience
macOS ADE profiles let you configure local administrator and optionally a standard user account. This will appear in both new and existing enrollment profiles and it will appear under the Account Settings section.
Enrollment Profiles
To configure the local admin settings for macOS LAPS, you must do so within the Enrollment Profile—there is currently no separate Device Configuration policy for macOS LAPS in Intune.
How to Access and Edit the Enrollment Profile
In the Intune admin center, go to:
Devices > macOS > Enrollment > Enrollment program tokens
- Click on your Enrollment Program Token (e.g., Intune Server).
- If you haven’t yet set up your MDM server with Apple Business Manager, you’ll need to complete that first.
- Once in the token view, go to the Profiles tab.
- Select an existing macOS enrollment profile and click Edit, or create a new one if needed.
From there, you can configure the local administrator account settings used during Automated Device Enrollment.
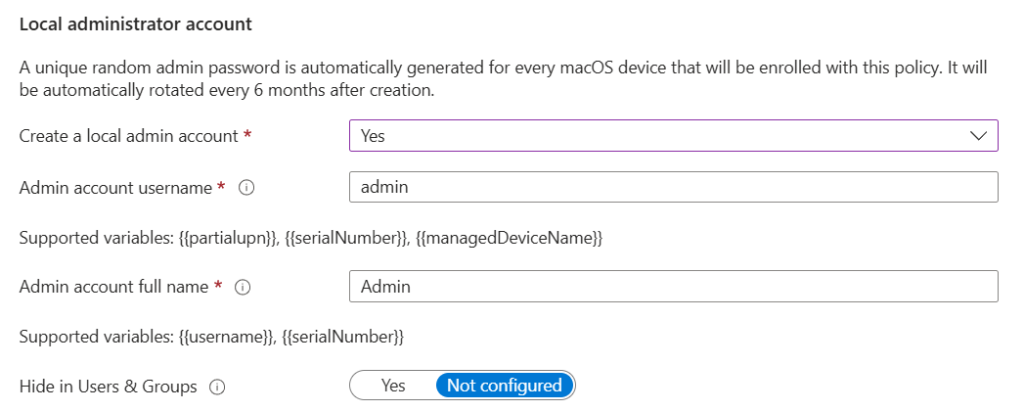
Create Local Accounts
If you create the local administrator account, you can specify the account username and it can use supported variables listed in the screenshot. This account will be the LAPS admin account that will generate a random password.
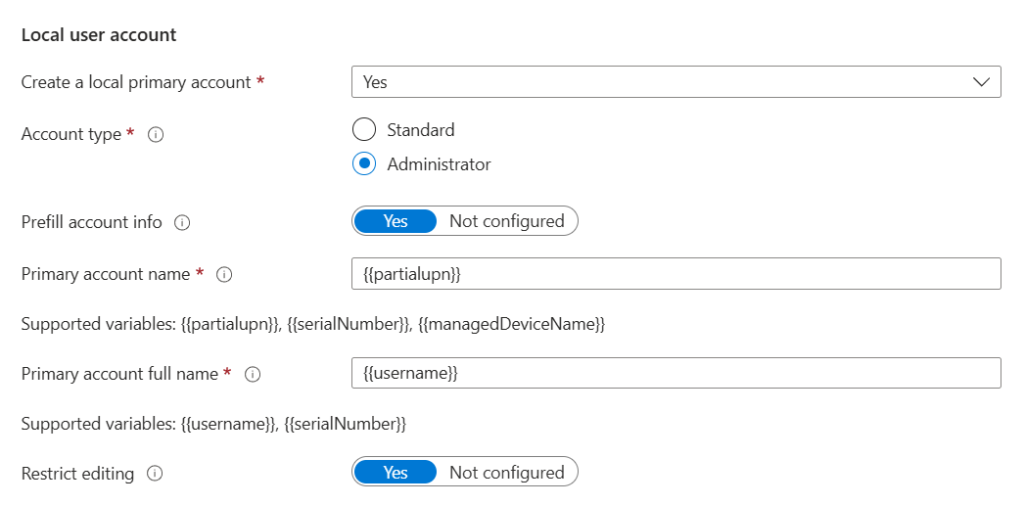
The second option is to create a local user account, which can be a standard user or administrator and you can also create this in addition to the LAPS admin account.
Admin Experience (How to Retrieve Password)
Unlike Windows LAPS, which allows policies to be deployed directly to existing machines, LAPS for macOS works differently as it must be configured during the device’s initial enrollment. Once a macOS device is enrolled into Intune, the system automatically generates a unique local admin password for that machine.
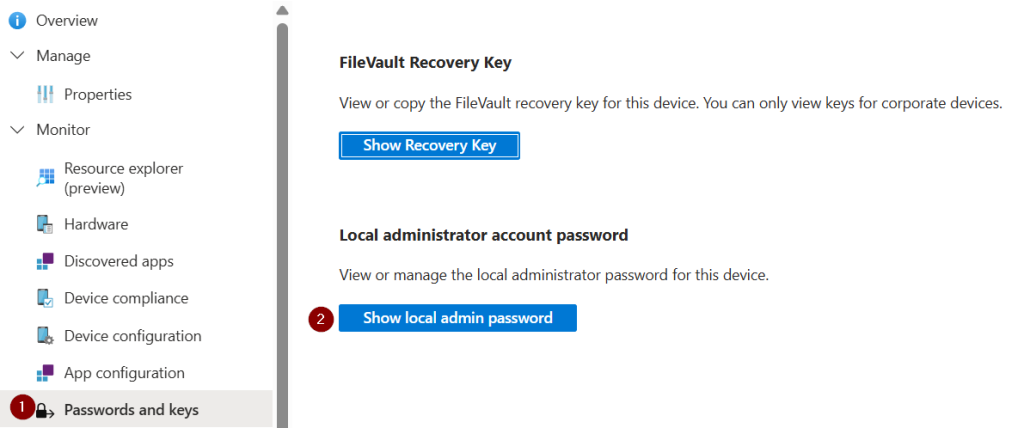
To retrieve the password:
- Navigate to the device in Intune
- Go to Properties
- Scroll to Passwords and keys
- Click Show local admin password
This reveals the password needed for local login to the macOS device.
After clicking on the Show local admin password button, the password should appear.
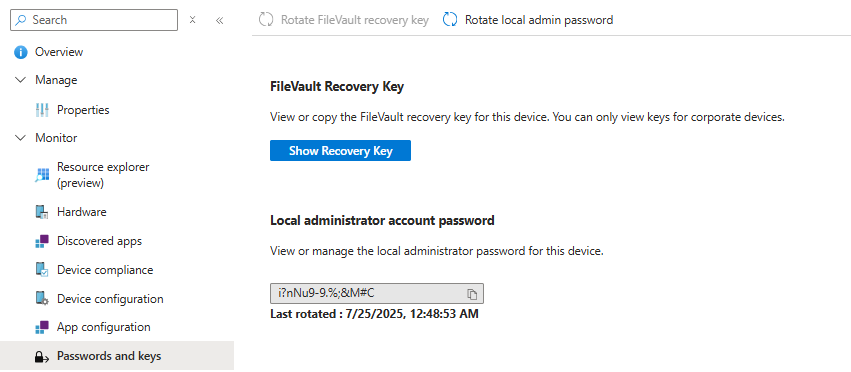
The LAPS password rotates automatically every six months. However, if you’ve shared the password and need to rotate it immediately, head to the device overview pane in Intune. Click the three dots in the top-right corner and select Rotate local admin password.
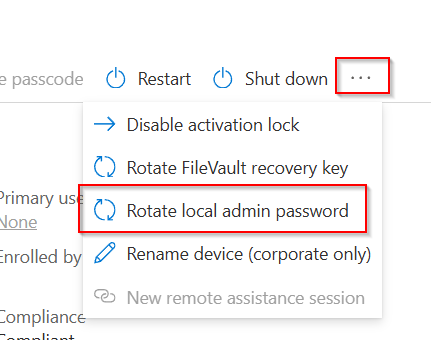
Behaviour with Device Compliance/Device Restrictions Password Policies
As mentioned at the beginning of this post, deploying Device Compliance and/or Device Restrictions policies with password requirements will trigger a password change prompt and a reboot at first login. According to Microsoft, this behavior is by design. If you do not have these policies set up, it should not prompt for a password change.
Below is an example of the password change prompt.
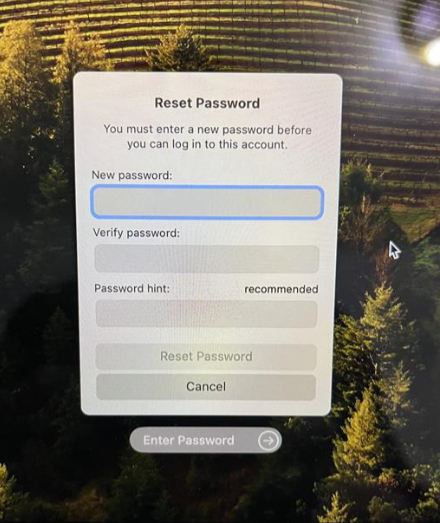
To remediate the LAPS admin password, follow these steps below. Note that the password change prompt should occur only once:
- Log in to the device using the LAPS admin password. When prompted, change the password.
- After signing in, rotate the local admin password and sync the device.
- Refresh the page and retrieve the updated LAPS password.
- Log out and log back in with new LAPS password. Intune should then resume control of the account.
Note: If you run into an issue rotating the local admin password, try again after 30 minutes. The Intune Product Team mentioned they are currently working on a hot fix.
Video Demonstration
To help you implement this solution, I’ve put together a detailed video that walks through the entire setup process and showcases the user experience from start to finish.
YouTube Link: https://www.youtube.com/watch?v=ZWB54Ph_f_Q
Considerations
Here are a few key considerations to keep in mind before rolling out LAPS for macOS:
- Having it apply only during enrollment. Existing devices will have to re-enroll to get the feature.
- RBAC permissions aren’t included in default roles. As discussed earlier, custom roles must be created.
- Password rotation is every 6 months unless manually triggered. Currently, there is no setting to change this.
Conclusion
Intune’s new macOS LAPS integration marks a significant step forward in securing Apple devices at scale. Where custom shell scripts once filled the gap, this update brings secure, automated admin account management natively into Intune, eliminating manual workarounds and reducing risk. Organizations managing macOS fleets should begin leveraging this powerful capability to modernize endpoint management and fortify device security.
If you would like to read more on LAPS for macOS, check out the Microsoft Documentation.